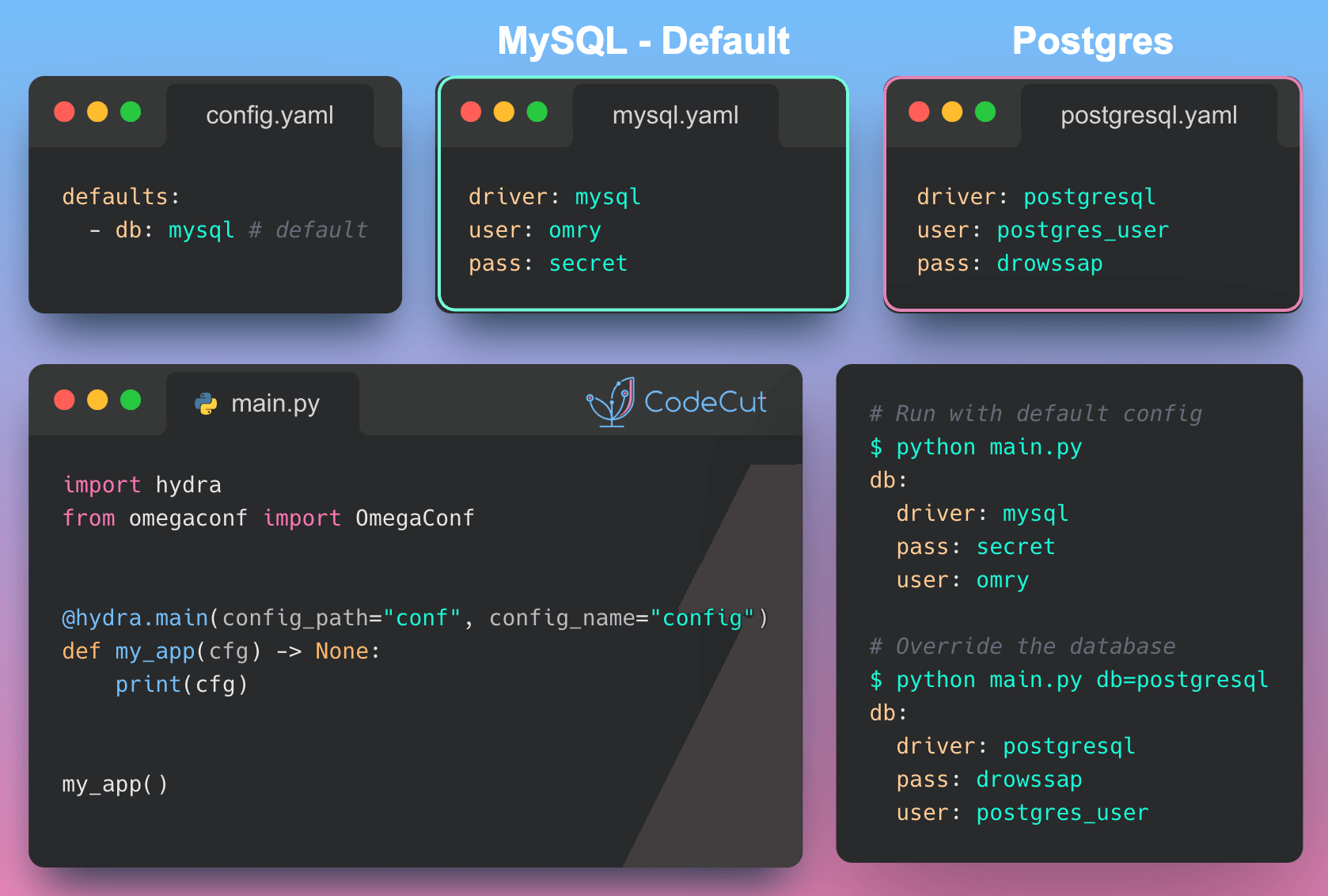
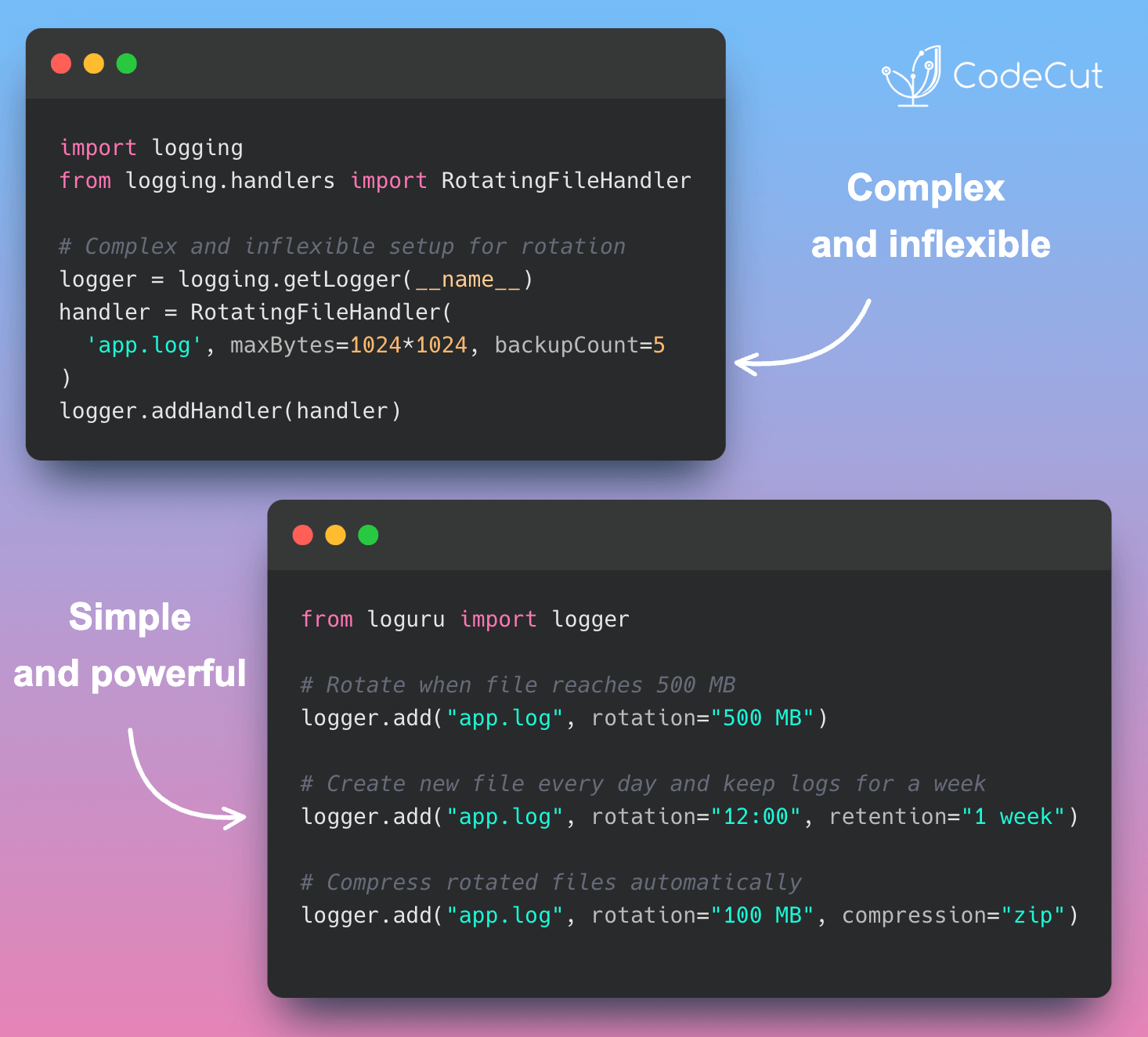
The Problem with Unchecked Pickle Loading
When working with machine learning models or serialized data in Python, it’s common to use the pickle module to save and load data.
However, loading pickle files directly without security checks can result in potential code execution vulnerabilities, especially when handling untrusted ML models or serialized data from external sources.
Let’s consider an example where we create a simple dummy model class, save it to a pickle file, and then load it without any safety checks.
import pickle
import numpy as np
# Create a simple dummy model class
class DummyModel:
def __init__(self):
self.weights = np.random.rand(10)
def predict(self, X):
return np.dot(X, self.weights)
# Create an instance of the dummy model
model = DummyModel()
# Save the model to a pickle file
with open("model.pkl", "wb") as f:
pickle.dump(model, f)import pickle
# No safety checks, potential for malicious code execution
with open("model.pkl", "rb") as f:
data = pickle.load(f) # Could execute harmful codeAs you can see, loading the pickle file without any safety checks can potentially execute malicious code, which is a serious security risk.
Introducing Fickling: A Safer Way to Handle Pickle Files
Fickling provides several ways to safely handle pickle files and ML models by detecting malicious content before execution. You can:
- Add runtime safety checks for all pickle operations
- Get a detailed analysis of potential security issues
Here’s an example of how to use Fickling to safely load a pickle file:
import fickling
fickling.always_check_safety()
with open("model.pkl", "rb") as f:
data = pickle.load(f)When we run this code, Fickling will raise an UnsafeFileError if it detects any potential security issues.